SquareX at Black Hat and DEF CON: Bring Our Browser Security Research to the World
SquareX at Black Hat and DEF CON: Bringing Our Browser Security Research to the World
Team SquareX Takes on Hacker Summer Camp in 2025

With the twin events of Black Hat USA and DEF CON 33, Las Vegas transformed into the cybersecurity capital of the world once again this August, and SquareX was there in full force. After an incredible “hacker summer camp” last year, we were back with ambitious plans: sharing groundbreaking browser security research, live demonstrations of our Browser Detection and Response (BDR) platform, multiple talks, workshops and even new open-source tools for the security community.
Black Hat USA: Showcasing how SquareX Secures Any Browser, Any Device
Walking into the Mandalay Bay Convention Center, the energy was palpable. Our team set up shop at Booth #6825 in Startup City, ready to showcase how BDR secures any browser and device. With 85% of employee work happening in browsers today, traditional SASE/SSE/EDR approaches simply aren’t cutting it anymore, and our booth was filled with interested conferencegoers eager to find out how they could bridge this security gap.

A definite highlight was our Founder Vivek Ramachandran’s presentation Browser-Native Security in a Browser First World, where he challenged the audience to rethink their security stack, demonstrating why EDRs, SASE/SSE solutions, and endpoint DLP tools fall short against modern browser-based threats. The talk discussed bleeding-edge attack techniques targeting employees directly in their browsers and covered how AI-powered browsers (and agents, as we recently disclosed) are a security liability.


Audrey Adeline from our Founder’s office also hosted a fireside chat — The Trailblazer’s Guide to Cybersecurity, which struck a different chord. Together with Jen Winters, the COO of Pacific Hackers Association, they had a candid sharing about their cybersecurity journeys and the challenges facing first-generation tech professionals.

The last day of Black Hat also saw a signing event for our latest book, The Browser Security Field Manual. Written in collaboration with Fortune 500 CISOs, this practical guide dissects the techniques adversaries use to compromise organizations through employee browsers. The blend of technical depth, real attack chains, and code snippets resonated with security practitioners hungry for actionable intelligence on browser threats — as shown by the constant stream of people looking to get their autographed copy.



Overall, Black Hat was a whirlwind of activity. The days were packed with productive meetings and insightful conversations with CISOs who are grappling with the same browser security challenges we’re solving. Between sessions, we caught up with old friends from across the industry, whilst forging new connections. Each evening, the team gathered for dinner — great food, shared stories from the day, and the kind of bonding that only happens when you’re all passionate about the same mission.





The energy was infectious, spirits were high, and every conversation was meaningful. Truly an experience to remember — and before we knew it, it was time for DEF CON.
DEF CON 33: Pushing the Boundaries of Browser Security Research
If Black Hat was about enterprise solutions, DEF CON was our playground for bleeding-edge research. We kicked things off at Demo Labs by showcasing two new open-source toolkits: Angry Magpie, which simulates sophisticated data splicing attacks that bypass traditional DLP solutions, and Copycat, a browser extension-based identity attacks simulator. Created by SquareX team members Jeswin Mathai, Pankaj Sharma, Xian Xiang Chang, Dakshitaa Babu, Tejeswar S Reddy, and Albin Antony, these toolkits address the testing and detection deficit in browser security — red teams lack tools to properly simulate browser-based attacks, while blue teams struggle to detect and respond to threats their monitoring systems can’t see.




The team also delivered two intensive workshops that went deep into emerging threats. Our Head of Cybersecurity Research, Nishant Sharma, conducted Serverless but Not Defenseless: A Security Deep Dive into Cloud Run at Cloud Village, equipping attendees with hands-on skills for securing Google Cloud Run deployments using DevSecOps principles and GCP-native tools.



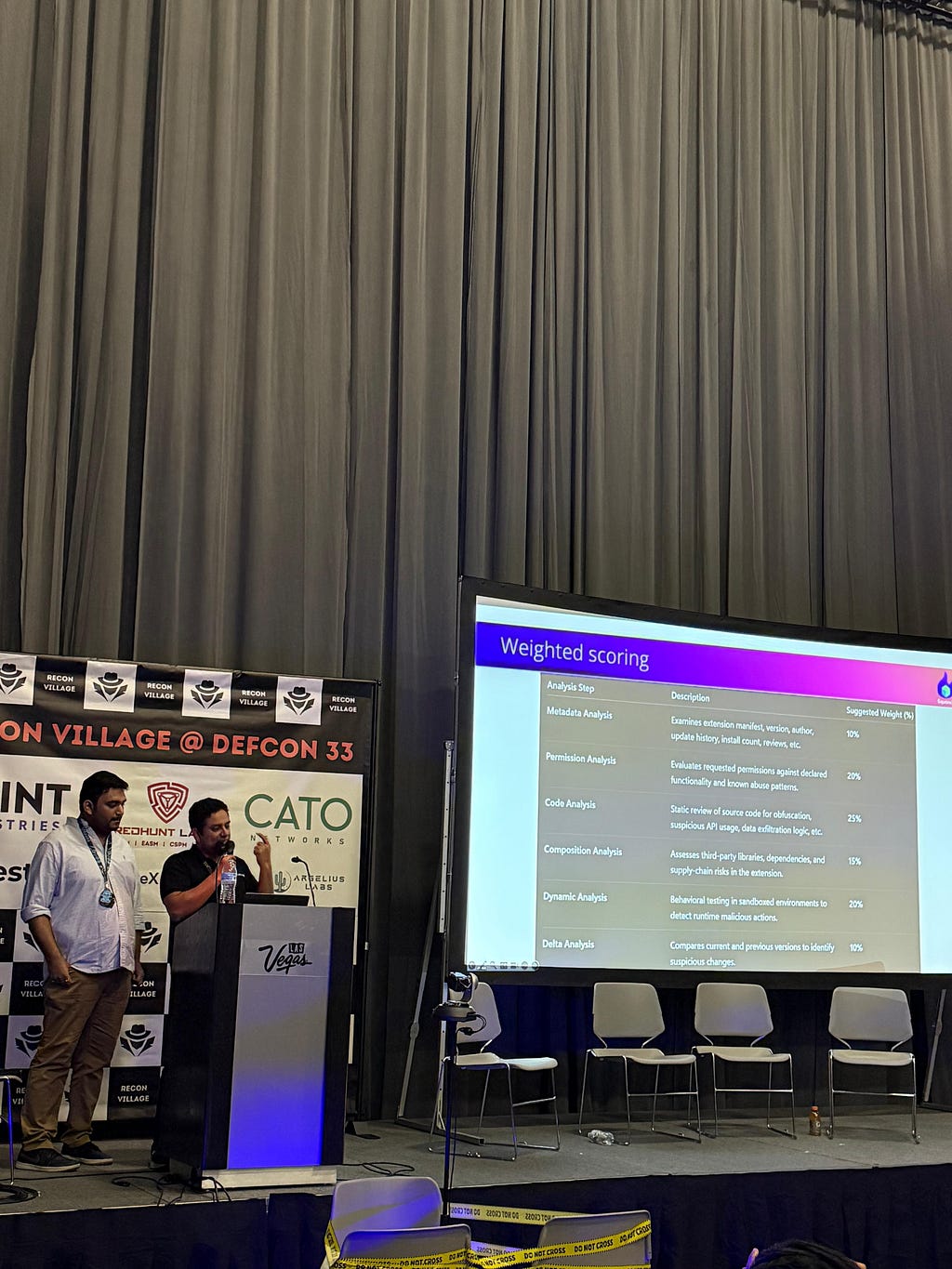
Nishant also collabrated with our Principal Software Engineer Shourya Pratap Singh on the Recon Village Talk Plug and Prey: Scanning and Scoring Browser Extensions. The talk introduced ExtHuntr, an open-source scanner that gives enterprises visibility into the unmonitored threat surface of browser extensions across their fleet— even assigning each extension a risk score.


The crescendo came on the final day with our main stage presentation: Passkeys Pwned: Turning WebAuthn Against Itself. Team members Shourya Pratap Singh, Jonathan Lin, and Daniel Seetoh took to the stage to demonstrate how attackers can proxy WebAuthn API calls to forge passkey authentication responses — a sobering reality check for organizations banking on passkeys as their password replacement strategy. The live demonstration showed this attack succeeding against sites that don’t enforce attestation or metadata checks — a common scenario among vendors today — and was even covered by publications such as SecurityWeek.



Beyond the talks and demonstrations, DEF CON is about community. We spent time catching up with old friends from the security world, swapping stories and sharing insights.



Another memorable stop was at the Hackers with Disabilities (HDA) village, for which our Senior SOC Lead, Frank Clark, was the lead. Besides learning about accessibility in cybersecurity, Frank showed our team members how the Hacker Chair works — and yes, it’s exactly as cool as it sounds.



Between sessions, we soaked in the unique atmosphere that only DEF CON delivers; the electric energy of thousands of hackers pushing boundaries together. We left Las Vegas feeling not just proud of the work we’d shared, but also imbued with a sense of community.



Closing Thoughts: Browser Security Is No Longer Optional
Looking back at our experience at both Black Hat USA and DEF CON 33 in 2025, we were proud to have presented our browser security research on these internationally renowned stages. From data splicing attacks to passkey vulnerabilities, it’s clear that browser-native security is no longer optional.
It’s natural: the browser is the new endpoint, and traditional security approaches that worked when browsers were mere website renderers don’t scale to today’s reality. Browsers are now full-fledged application platforms handling critical workflows, sensitive data, and identity management — and they demand purpose-built security solutions.
Ever since we presented Last Mile Reassembly Attacks at DEF CON 32 last year, SquareX has grown even more. We’ve delivered seminal talks, released open-source tools for security teams and published market-leading research that’s reshaping how the industry thinks about browser security. Today, SquareX is the most recognized brand in browser security — a testament to our team’s dedication and innovation.
But we’re just getting started. Stay tuned for more novel research, and if you want to learn more about how SquareX can secure any browser on any device for your organization, the best place to start is our website. Till the next conference!
SquareX at Black Hat and DEF CON: Bring Our Browser Security Research to the World was originally published in SquareX Labs on Medium, where people are continuing the conversation by highlighting and responding to this story.
The post SquareX at Black Hat and DEF CON: Bring Our Browser Security Research to the World appeared first on Security Boulevard.
>>More
