Exposure Management Beyond The Endpoint
Relying on an endpoint-centric approach to exposure management can leave you with blind spots that increase risk. You need to see your environment like an attacker does.
Key takeaways:
- Long remediation cycles and difficulty prioritizing risk are significant challenges for security teams.
- Exposure management capabilities bolted onto existing security tools result in dashboard fatigue and manual processes that slow response time.
- Unified exposure management gives teams the context and intelligence they need and integrates into existing systems of record to speed remediation times.
How do you scale with the threat landscape? That’s one of the greatest challenges facing security organizations.
An attacker’s entry point can be a critical vulnerability on a public-facing server, a severe misconfiguration in the cloud or an overprivileged permission in an identity system. Threat actors only need to exploit a single misconfiguration or vulnerability to gain a toehold into an environment, where they quickly pivot to living off the land techniques, using legitimate tools to perform lateral movement and privilege escalation. They’re leveraging a broad attack surface that includes AI, cloud environments, web applications, APIs, identity systems, operational technology (OT) and IoT. And overwhelmed security teams are over-rotating on an “assumed breach” mentality.
To understand the scope of the challenge, consider this: From 1999 to 2019, there were 124,000 registered CVEs tracked by MITRE. From 2019 to 2024 that number nearly doubled to 240,000 and it’s currently at 300,000.
Security tool vendors with expertise in a specific area, such as endpoint detection and response (EDR), may offer add-on vulnerability management or exposure management services to their offerings. It may seem easy to add these capabilities onto an existing deployment. But relying on such offerings to manage a complex environment can result in blind spots that increase risk.
In order to scale with the threat landscape, security teams need to be able to see their environment just as an attacker does.
Yet, 42% of respondents to a recent Tenable webinar poll combine multiple tools and a homegrown approach to secure their environments, while another 12% rely primarily on an endpoint security vendor’s tools.
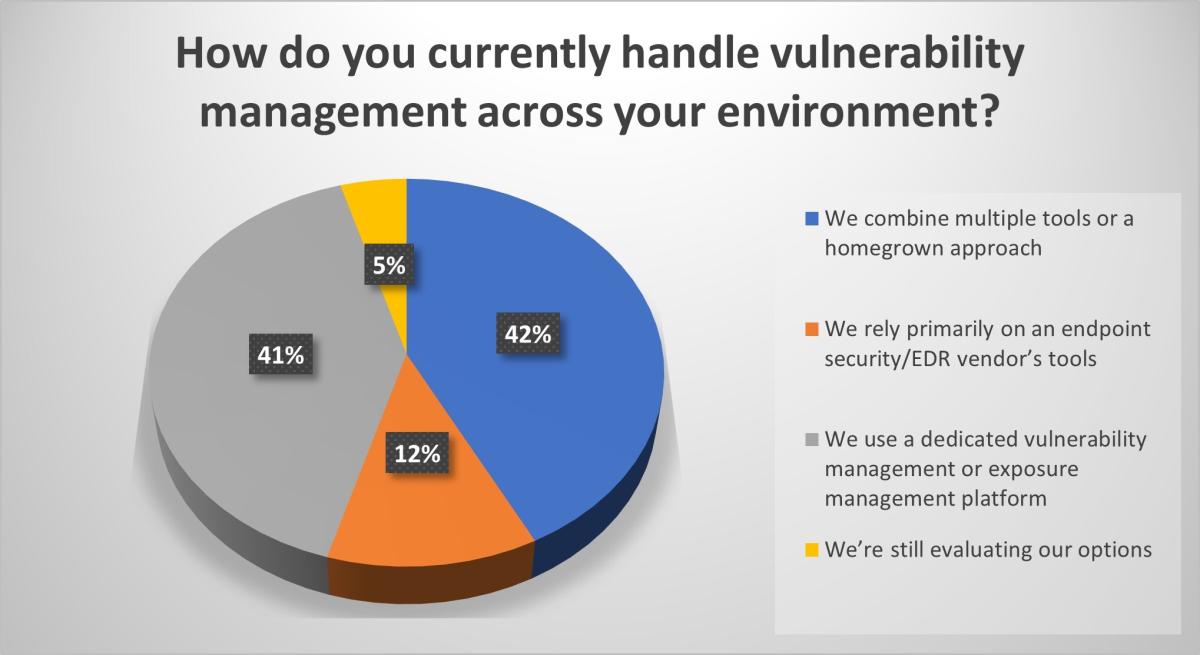
Modern attackers rarely focus on just one part of the infrastructure, and an endpoint-centric view creates dangerous blind spots that attackers can exploit. The Tenable webinar Beyond the Endpoint: Exposure Management That’s Proactive outlined the real-world gaps created by an endpoint-centric security approach, including missed exposures, reliance on vendor coverage, detection delays and compliance difficulties.
“You want to take an ‘assumed breach’ mindset? That doesn’t mean you have to have an ‘accept breach’ mindset,” said John Hendley, VP of Cybersecurity for Coalfire, a Tenable MSSP partner, during the webinar. “We don’t need to make it easier for folks to try to get in and do nefarious things.”
Hendley noted that he sees a lot of dashboard fatigue among customers who cobble together multiple tools and then struggle to attain a clear understanding of where they are most at risk.
“There are two constants in security: time and context,” said Raymond Carney, senior director, Tenable Research. “A lot of times we tend to think of security as a purely technical sort of acumen we’re applying. But to be successful we have to elevate it to business terms.” This requires understanding the potential impact a given vulnerability can have on the business, as well as being able to contextualize that for C-level executives who want to know if the business is at risk.
An endpoint-centric approach to security can’t provide the context organizations need to proactively reduce risk. Siloed tools not only increase dashboard fatigue, they make it difficult to integrate remediation workflows into IT systems of record such as Jira and ServiceNow.
More than a third of webinar attendees (38%) cited long remediation cycles as their biggest day-to-day challenge, while 31% have difficulty validating and prioritizing risk.
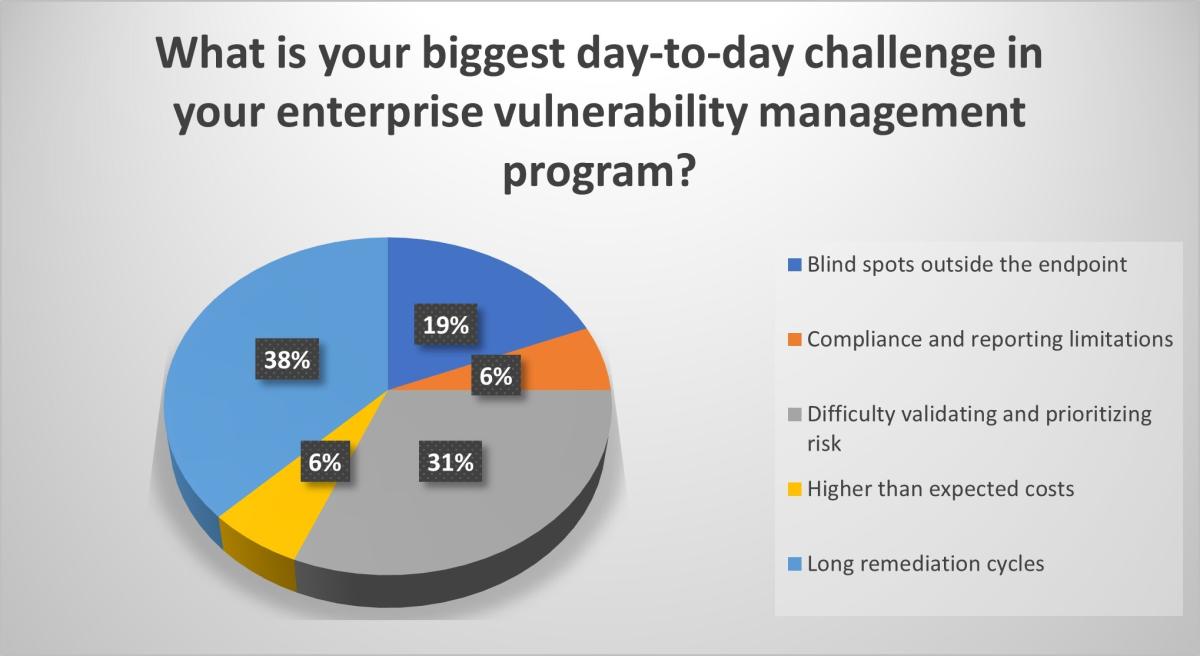
“What’s great about Tenable is that because it has such rich integrations, it can feed that data into your systems of record, where your data lives, where your teams go and fix things,” said Hendley. “That’s a really powerful force multiplier.”
5 factors that set Tenable exposure management apart
A unified exposure management platform like Tenable One gives security teams the context and intelligence they need to reduce risk across the complex attack surface. Here are five key ways Tenable One stands out:
- Data sources: Many endpoint vendors pull in data from other sources, which can introduce lag times that can slow remediation efforts. The Research Special Operations team in Tenable Research analyzes over 50 trillion data points, allowing Tenable to provide coverage for over 40% more Windows server vulnerabilities and 16% more CVEs than competitors. An average of four plugin feeds are published daily.
- Transparency: Tenable plugin pages clearly show what’s covered in the current feed, what’s in the pipeline and the audit and compliance coverage available.
- Vulnerability intelligence: Tenable Research is constantly looking at observable evidence in the threat landscape, providing customers with the analyses and contextualized exposure intelligence required to manage risks to critical business assets. Their goal? Cut through the noise and deliver critical intelligence about the most dangerous cyber threats emerging right now. Since the beginning of 2024 our advisory content, vulnerability watches and emerging data has preceded the publication of the CISA Known Exploited Vulnerabilities (KEV) catalog by an average of eight and a half days.
- Prioritization: Being able to boil down the 300,000 published CVEs to the 800 flagged as critical by the Tenable Vulnerability Priority Rating and further to the 17 or 20 a year that are most impactful helps you focus in on the areas that we’re most likely to be subject to breach and the potential impact on the business.
- Asset management: The Tenable platform is designed to help you identify the systems you didn’t know you had, so you have an attacker’s view of your environment. This is more important than ever with the increase in AI usage and the growth of shadow AI.
Conclusion
Endpoint-centric security is insufficient for the modern attack surface. Relying on EDR vendor tools can leave you with critical blind spots. Modern attackers exploit cloud misconfigurations, web applications, APIs, identity systems and OT/IoT, all of which endpoint tools were not built to see or assess.
Overcoming security challenges requires moving beyond dashboard fatigue and manual processes. Integrating a single exposure management platform into an organization’s existing systems of record (e.g., ServiceNow, Jira) automates ticket creation and routing, transforming data into efficient, trackable remediation workflows.
Effective exposure management makes it possible to home in on what matters most by providing explainable, contextual intelligence based on actual threat actor activity so you can focus on the highest-impact risks. Tenable's RSO team leverages massive data analysis to provide superior vulnerability coverage and crucial advanced warning of days or weeks on emerging threats, compared to relying on slower external sources like the National Vulnerability Database (NVD) or the CISA KEV.
A unified exposure management platform gives you a contextual view of risk that encompasses vulnerabilities, misconfigurations, overprivileged identities and other weaknesses so you can proactively identify and close gaps across the entire attack surface.
Learn more
View the on-demand webinar, Beyond the Endpoint: Exposure Management That’s Proactive

The post Exposure Management Beyond The Endpoint appeared first on Security Boulevard.
>>More
