Cybersecurity Snapshot: 2025 Rewind: Essential Cyber Insights, Strategies and Tactics
In this special year-end edition, we revisit critical advice from our cybersecurity experts on AI, exposure management, cloud, vulnerability management, OT, and critical infrastructure.
Key takeaways
- Combating AI threats: Counter autonomous agentic AI attacks and shadow usage by enforcing strict governance and elevating basic cyber hygiene to prevent massive-scale breaches.
- Adopting exposure management: Align security with business objectives by adopting a unified exposure management program to preemptively prioritize and remediate the most critical threats first.
- Securing cloud and critical infrastructure: Reduce attack surfaces by rigorously managing identities to stop "permission creep," implementing just-in-time (JIT) access, and maintaining precise asset inventories.
In case you missed it, we’re recapping standout guidance from Tenable experts to help you with agentic AI attacks, overprivileged identities, risk-based metrics, OT inventories, vulnerability prioritization, and geopolitical threats.
1 - Defending against agentic AI and managing shadow AI risks
The emergence of agentic AI tools that act autonomously has shifted the threat landscape. Here is how Tenable experts addressed security and governance in this new era.
In "Agentic AI Security: Keep Your Cyber Hygiene Failures from Becoming a Global Breach," Tenable Chief Security Officer Robert Huber warns that the weaponization of legitimate agentic AI coding tools, such as Anthropic's Claude Code, "proves that neglecting fundamental cyber hygiene allows malicious AI to execute massive-scale attacks with unprecedented speed and low skill."
The good news is that even AI-powered attacks can’t succeed if you’ve closed your most critical exposures, impeding lateral movement and privilege escalation. “Elevating the standard of basic security hygiene is essential for our collective defense,” he wrote.
Blake Kizer recommends in "A Practical Defense Against AI-led Attacks" a unified, preemptive and predictive exposure management program rooted in security fundamentals. By defining the new AI attack surface and fighting AI with AI, “the winner will be the team that builds the best partnership between human intuition and algorithmic speed,” writes Kizer, a Staff Information Security Engineer at Tenable.
Meanwhile, in "FAQ About Model Context Protocol (MCP) and Integrating with AI for Agentic Applications," Chad Streck notes that while MCP standardizes connecting data to large language models (LLMs), it raises security concerns developers must address.
How MCP Works
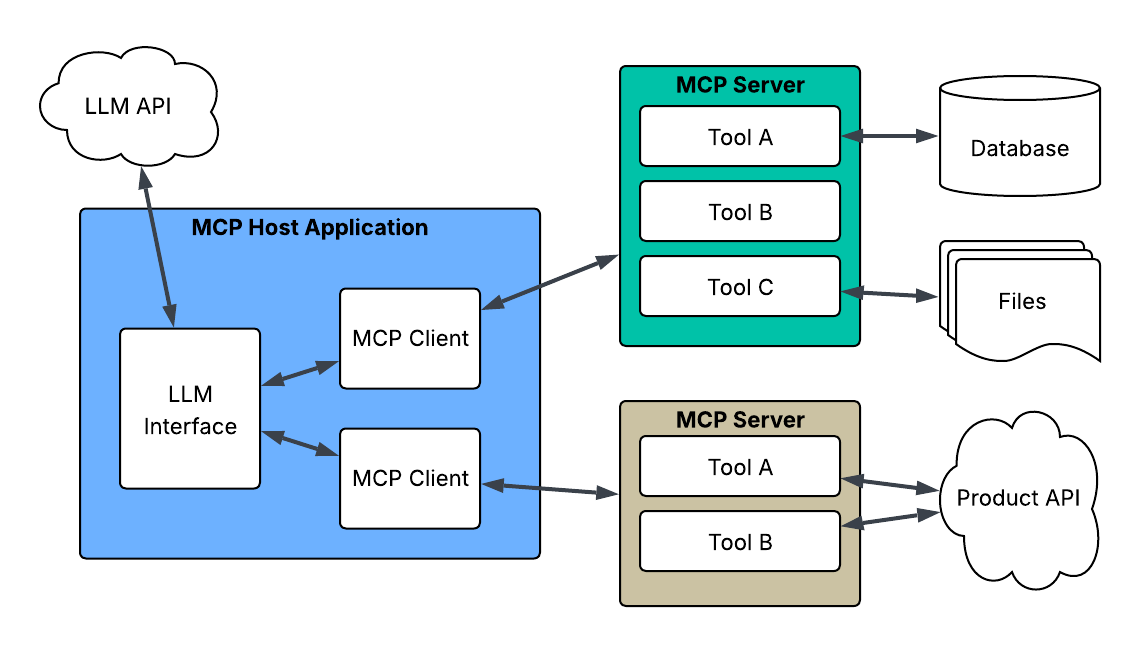
(Source: Tenable, April 2025)
Streck, a Staff Research Engineer at Tenable, recommends:
- Detecting and inventorying your MCP installations and configurations
- Controlling access and monitoring the resources MCP servers tap
- Training staff on secure MCP usage
Meanwhile, in "Security for AI: How Shadow AI, Platform Risks, and Data Leakage Leave Your Organization Exposed," Damien Lim, a Senior Product Marketing Manager at Tenable, tackles the dangers of employees’ AI usage: shadow AI; the risks from approved AI tools; and the potential exposure of sensitive information.
To mitigate the risk of employees exposing sensitive data, Lim advises benchmarking your organization against best practices outlined in "Security for AI: A Practical Guide to Enforcing Your AI Acceptable Use Policy," including:
- List approved and prohibited tools.
- Create data privacy and security guidelines.
- Categorize AI use into Permitted, Prohibited, and Controlled.
2 - Tackling cloud permission creep and exposed secrets
Is your cloud environment suffering from excessive access rights? Tenable experts emphasize rigorous hygiene and identity governance.
In "Don’t Let Your Cloud Security Catch a Bad Case of Permission Creep," Thomas Nuth warns that over-privileged identities create attacker pathways.

Nuth, Head of Cloud Product Marketing at Tenable, suggests automating least privilege enforcement via a CNAPP integrated with an exposure management platform that combines:
- Identity discovery
- Contextual risk correlation and prioritization
- Automated detection and remediation of excessive permissions
One effective method to combat overprivileged identities is via just-in-time (JIT) access. Xavier Allan, Senior Cloud Security Engineer at Tenable, explores this strategy in "How To Implement Just-In-Time Access: Best Practices and Lessons Learned." Allan notes that with JIT, "privileges are granted temporarily on an as-needed basis," which reduces static entitlements and lowers the risk of compromised accounts.
Based on Tenable’s internal JIT adoption, Allan offers tips including:
- Communicate continuously during the transition.
- Help teams feel comfortable with the JIT process before and during the migration.
- Educate teams on JIT capabilities to drive adoption.
However, identity is only part of the equation; digital debris also poses a significant risk. In "How To Clean Up Your Cloud Environment Using Tenable Cloud Security," Stephanie Dunn, Staff Cloud Security Engineer at Tenable, points out that old and unused cloud resources create risks.
To clean up your cloud environment, Dunn recommends determining:
- The age of your resources
- Active and inactive cloud accounts
- Users’ cloud account access
- Public-facing cloud resources
- Resources types and accessed data
Finally, Ryan Bragg addresses the hidden dangers of credentials in "Secrets at Risk: How Misconfigurations and Mistakes Expose Critical Credentials." Bragg writes that "poor secrets management" undermines security by exposing API keys, tokens, access keys and even login credentials.
Bragg, a Senior Cloud Security Solutions Engineer at Tenable, offers best practices to protect secrets, including:
- Map where secrets reside and implement controls.
- Avoid using long-term credentials, such as passwords and keys.
- Implement lifecycle policies to regularly rotate secrets.
- Don’t hardcode secrets in bootstrap scripts, environment variables, and tags.
3 - Shifting to exposure management
One thing is clear: Exposure management is the key for successfully protecting your organization against today’s relentless and evolving cyber threats. By going beyond traditional vulnerability management, a true exposure management platform like Tenable One helps you preemptively pinpoint, prioritize and close your most critical exposures while shrinking your hybrid attack surface.
As an exposure management pioneer and leader, Tenable is at the forefront of this approach to cybersecurity. Through our Exposure Management Academy, we constantly share practical guidance, case studies and peer insights to help you on your exposure management journey.

In a two-part series, Tenable CSO Robert Huber outlines his own team's evolution. In "How Tenable Moved From Siloed Security to Exposure Management," Huber explains the move away from fragmented security practices. He follows up in "How Exposure Management Has Helped Tenable Reduce Risk and Align with the Business" by detailing how this shift helps reduce risk and better align with the business.
“Our goal is to uplevel all our conversations to align with the business, demonstrating the impact of security on revenue, services and overall business objectives,” Huber writes. “More than a mere buzzword, exposure management is a necessary evolution of how organizations approach cybersecurity.”
Understanding peer perspectives is also crucial. In "How Top CISOs Approach Exposure Management in the Context of Managing Cyber Risk," Huber cites reports from the new Exposure Management Leadership Council, a CISO working group sponsored by Tenable.

“Council members see the potential for exposure management to help them create a standardized, repeatable and defensible process for measuring and reporting on risk,” Huber writes.
Budgeting for this transition is another common hurdle. Discussing a study conducted by Enterprise Strategy Group in partnership with Tenable, Hadar Landau, a Product Marketing Manager at Tenable, notes in "How to Future-Proof Your Cybersecurity Spend" that "complexity is driving a growing number of organizations to increase their exposure management budgets."
Landau outlines five keys to future-proof your exposure management spend:
- A unified platform for ecosystem-wide data ingestion
- Visibility into AI system usage
- Automated prioritization of high impact risks
- Identification of toxic risk combinations
- Maximizing the value of existing security investments
In "How to Use Risk-Based Metrics in an Exposure Management Program," Tenable Information Security Engineers Arnie Cabral and Jason Schavel say metrics are fundamental to each stage of the exposure management lifecycle.
Specifically, they say that risk-based metrics provide:
- The context to understand scan tools’ raw data
- An objective basis for exposure prioritization
- Validation on success and risk reduction
- Clear reporting to mobilize teams and secure resources
4 - Enhancing OT security with identity and inventory
Can you secure your critical infrastructure against sophisticated threats without grinding operations to a halt? As Tenable experts explain, securing operational technology (OT) without disrupting production requires preemptive remediation and identity security.
In "How to Remediate Risk to Critical OT/IoT Systems without Disrupting Operations," Meir Asiskovich, Tenable’s Senior Director of Product Management for Tenable OT Security, argues that adopting a proactive approach allows teams to "reduce risk and eliminate downtime" simultaneously. You also need an exposure management program.
“By unifying data from IT, OT, IoT, cloud and identities, we’re able to deliver a seamless workflow, complete asset inventory and context-aware prioritization that legacy OT security tools and point solutions can’t match,” Meir writes.
In "Identity Security Is the Missing Link To Combatting Advanced OT Threats," Chris Baker, OT Security Sales Manager at Tenable, warns that attackers use living-off-the-land (LotL) techniques that "exploit identity vulnerabilities to infiltrate critical infrastructure." Integrating identity security with unified exposure management is essential to detect these subtle intrusions.
He outlines key aspects of an effective OT security program, including:
- Understanding your assets
- Monitoring for anomalies
- Limiting privilege escalation
- Hardening Active Directory
- Identifying attack paths
In "How to Apply CISA’s OT Inventory and Taxonomy Guidance for Owners and Operators Using Tenable," we break down federal recommendations, underscoring how a detailed asset inventory and taxonomy are "not only the foundation of a defensible security posture, they’re also essential for resilient operations."
CISA offers a systematic process to develop and maintain a record of your organization’s OT assets, as illustrated below.

Source: U.S. Cybersecurity and Infrastructure Security Agency (CISA), Foundations for OT Cybersecurity: Asset Inventory Guidance for Owners and Operators, August 2025
5 - Improving vulnerability management with better visibility, prioritization and automation
In 2025, as the speed of vulnerability exploitation grew, Tenable looked at the critical stages of the vulnerability lifecycle, from closing disclosure gaps to automating remediation.
In "Why Early Visibility Matters: Risk Lurks in the Vulnerability Disclosure Gaps," Lucas Tamagna-Darr highlights the importance of having timely information about vulnerabilities and the risk they present.
“Because Tenable drives its coverage directly from vendor advisories, a majority of our coverage is available within 12-24 hours of the initial disclosure of a vulnerability,” writes Tamagna-Darr, Senior Director of Engineering and Research Solutions Architect at Tenable.
Damien McParland discusses the evolution of prioritization in "Narrowing the Focus: Enhancements to Tenable VPR and How It Compares to Other Prioritization Models." McParland explains how updates to Tenable’s Vulnerability Priority Rating (VPR), including enriched threat intelligence, AI-driven insights and explainability, and contextual metadata, have further boosted VPR’s prioritization efficiency.

The VPR enhancements make it “twice as efficient as the original version at identifying CVEs that are currently being exploited in the wild or are likely to be exploited in the near term,” writes McParland, Staff Data Scientist at Tenable,
Finally, effective prioritization must lead to rapid action. Allison Eguchi addresses the challenges of remediation in "Stop Patching Panic: Ditch Slow Manual Patching and Embrace Intelligent Automation." Eguchi, a Tenable Product Marketing Manager, warns that "manual patching leaves your organization exposed" and highlights how Tenable Patch Management offers customizable rules and guardrails to automate updates without causing business disruption.
6 - Managing geopolitical cyber risks and federal cloud modernization
Does it feel like your organization’s threat landscape shifts every time a new headline breaks on the world stage? It’s a topic Tenable experts have unpacked, looking at how global instability and federal modernization mandates are reshaping the responsibilities of security leaders.
James Hayes addresses the fatigue many defenders are experiencing in "Geopolitics Just Cranked Up Your Threat Model, Again. Here’s What Cyber Pros Need to Know." Hayes, Senior Vice President of Global Government Affairs at Tenable, writes: "If it feels like your entire cybersecurity program is once again operating on a geopolitical fault line, you're not imagining things."
His recommendations for cybersecurity teams include:
- Build geopolitical risk into your threat models.
- Pressure-test your supply chain visibility.
- Track policy shifts like you would threat intel.
- Advocate for the resources you need.
- Routinely assess your posture management.
- Take a proactive stance.
In "Navigating a Heightened Cyber Threat Landscape: Military Conflict Increases Attack Risks," Tenable CSO Robert Huber argues that the "current geopolitical climate demands a proactive, comprehensive approach to cybersecurity" rather than a reactive stance.
To strengthen your cyber defenses in this heightened threat environment, Huber’s recommendations include:
- Use strong passwords and enforce a strong password policy
- Change default passwords, especially on OT hardware
- Scan for and patch vulnerabilities in assets exposed to the internet
- Enable multi-factor authentication (MFA)
- Identify and prioritize your most valuable assets for remediation
- Develop a remediation plan and continue to test and improve it
Meanwhile, the federal government faces its own specific hurdles when adopting cloud computing. In "Securing Federal Cloud Environments: Overcoming 5 Key Challenges with Tenable," Huber explains how Tenable Cloud Security helps federal agencies overcome these obstacles:
- Limited visibility across complex cloud environments
- Identity and access complexity
- Operational complexity and tool sprawl
- Rapidly evolving threats and new attack vectors
- Misconfigurations and compliance gaps

The post Cybersecurity Snapshot: 2025 Rewind: Essential Cyber Insights, Strategies and Tactics appeared first on Security Boulevard.
>>More
